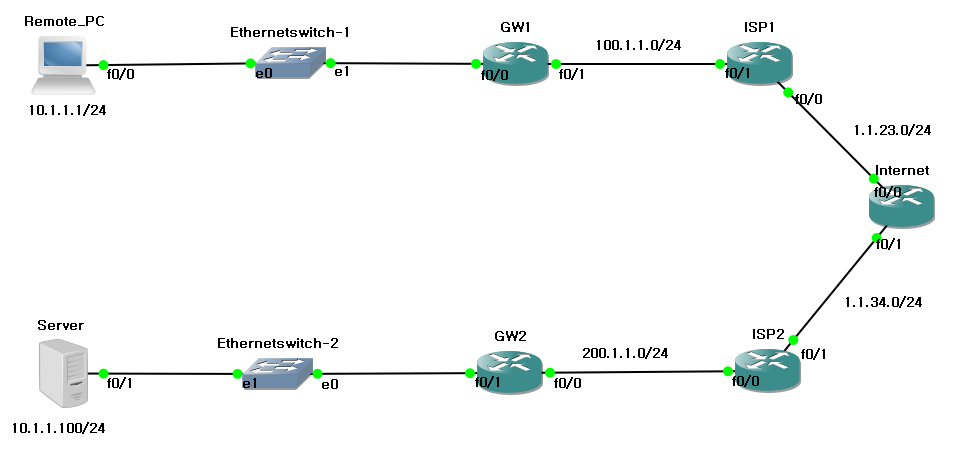
기본 설정 및 routing
# Remote_PC
int f 0/0
ip add 10.1.1.1 255.255.255.0
no shut# Server
int f 0/1
ip add 10.1.1.100 255.255.255.0
no shut# GW1
int lo 0
ip add 100.1.1.1 255.255.255.0
exi
int fa 0/1
no shut
pppoe enable
pppoe-client dial-pool-number 1
exi
int dialer 1
ip unnumbered lo 0
ip mtu 1454
encapsulation ppp
dialer pool 1
dialer-group 1
ppp authentication chap callin
ppp chap hostname cisco
ppp chap password cisco
exi
ip route 0.0.0.0 0.0.0.0 dialer 1
dialer-list 1 protocol ip permit# GW2
int lo 0
ip add 200.1.1.1 255.255.255.0
exi
int fa 0/0
no shut
pppoe enable
pppoe-client dial-pool-number 1
exi
int dialer 1
ip unnumbered lo 0
ip mtu 1454
encapsulation ppp
dialer pool 1
dialer-group 1
ppp authentication chap callin
ppp chap hostname cisco
ppp chap password cisco
exi
ip route 0.0.0.0 0.0.0.0 dialer 1
access-list 1 permit any
dialer-list 1 protocol ip list 1# ISP1
int fa 0/0
no shut
ip add 1.1.23.2 255.255.255.0
exi
int fa 0/1
no shut
ip add 100.1.1.2 255.255.255.0
exi
ip route 0.0.0.0 0.0.0.0 1.1.23.3
vpdn enable
vpdn-group 1
accept-dialin
protocol pppoe
virtual-template 1
exi
int fa 0/1
pppoe enable
exi
username cisco password cisco
int virtual-template 1
ppp authentication chap
mtu 1454
ip unnumber fa 0/1# ISP2
int fa 0/1
no shut
ip add 1.1.34.4 255.255.255.0
exi
int fa 0/0
no shut
ip add 200.1.1.2 255.255.255.0
exi
ip route 0.0.0.0 0.0.0.0 1.1.34.3
vpdn enable
vpdn-group 1
accept-dialin
protocol pppoe
virtual-template 1
exi
int fa 0/0
pppoe enable
exi
username cisco password cisco
int virtual-template 1
ppp authentication chap
mtu 1454
ip unnumber fa 0/0# Internet
int fa 0/0
no shut
ip add 1.1.23.3 255.255.255.0
exi
int fa 0/1
no shut
ip add 1.1.34.3 255.255.255.0
exi
ip route 100.1.1.0 255.255.255.0 1.1.23.2
ip route 200.1.1.0 255.255.255.0 1.1.34.4
pppoe 설정을 먼저 해준다
# GW1
ping 200.1.1.1 so 100.1.1.1
GW1 > GW2 통신 확인
xconnect 설정
# GW1
pseudowire-class L2TPv3-GW1<->GW2
encapsulation l2tpv3
ip local int lo 0
exi
int fa 0/0
no shut
xconnect 200.1.1.1 12 pw-class L2TPv3-GW1<->GW2
exi# GW2
pseudowire-class L2TPv3-GW1<->GW2
encapsulation l2tpv3
ip local int lo 0
exi
int fa 0/1
no shut
xconnect 100.1.1.1 12 pw-class L2TPv3-GW1<->GW2
exi
xconnect 설정을 해준다
# GW1, GW2
show xconnect all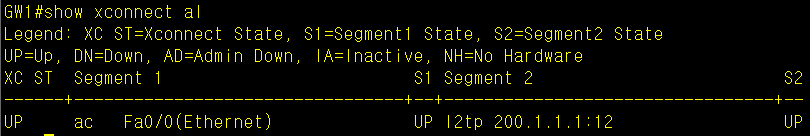
GW1,2에서 xconnect 확인
IPSec 설정
# GW1
access-list 100 permit 115 host 100.1.1.1 host 200.1.1.1
crypto isakmp policy 10
authentication pre
encryption aes 128
hash md5
group 2
lifetime 1000
exi
crypto isakmp key 6 cisco address 200.1.1.1
crypto ipsec transform-set BB esp-des esp-md5
exi
crypto map CC 10 ipsec-isakmp
set peer 200.1.1.1
set transform-set BB
match add 100
exi
int dialer 1
crypto map CC# GW2
access-list 100 permit 115 host 200.1.1.1 host 100.1.1.1
crypto isakmp policy 10
authentication pre
encryption aes 128
hash md5
group 2
lifetime 1000
exi
crypto isakmp key 6 cisco address 100.1.1.1
crypto ipsec transform-set BB esp-des esp-md5
exi
crypto map CC 10 ipsec-isakmp
set peer 100.1.1.1
set transform-set BB
match add 100
exi
int dialer 1
crypto map CC
IPSec 설정을 해준다
# Server
traceroute 10.1.1.1
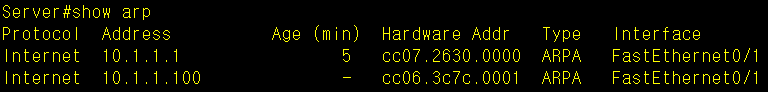
show arp
# GW1, GW2
show crypto engine connections active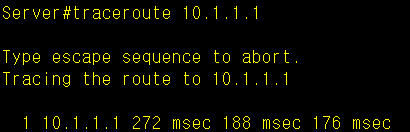

실제로는 떨어져 있지만 인접한 것처럼 보인다